As an energy expert, it’s difficult to escape news and commentary about EPA’s Final Clean Power Plan. However, I’m not a lawyer, but someone interested in how to make sense of the plan when it comes to cybersecurity and energy markets. More important, I’ve asked myself if the Clean Power Plan is just a speed bump or really a rule that is masking a megatrend. I’m leaning toward the latter when it comes to the energy sector, but have specific ideas when it comes to cybersecurity and ensuring reliable secure supplies and reasonable prices of electricity, natural gas, crude oil and refined petroleum products.
Megatrend or Speed Bump?
The EPA’s Clean Power Plan nudges the power system’s reliance on natural gas in the near term and on renewables in the future. In doing so, it reduces the diversity of the current power system made possible from power plants that rely on coal, nuclear and oil-fired generation. Overall, cybersecurity risks will increase on natural gas-fired power plants and also on coal and nuclear power plants that are being phased out.
Despite all the commotion over the Clean Power Plan’s potential effects on carbon intensive industries like coal, the underlying reason has been cheap and abundant natural gas and regulations to curb other forms of pollution. Cheap and abundant natural gas is a megatrend that has been underestimated since shale gas started to get on people’s radar in 2007 and 2008.
I also believe that individual State Renewable Energy Standards and the willingness of electric utilities to sign long-term power supply contracts with wind and solar developers along with declining product costs account for the grow of renewables. Despite all the hoopla about tax incentives, renewables are here to stay. They may even take center stage if utility scale electric storage replicates renewable energy’s growth. In that case natural gas as a power fuel may find itself in the company of coal industry.
The Clean Power Plan's Risks to Assets
The Clean Power Plan will do the following:
- Throw coal power plants under the bus with the help of EPA’s Mercury and Air Toxics regulations,
- Uses natural gas as a bridge fuel to reach the “promised land” and integrate renewable power into the grid,
- Incent development of utility-scale electric storage as well as distributed energy electric storage devices,
- Make room for Solar, Wind and Energy Efficiency to take center stage.
The last item above is really the ultimate goal. U.S. Electricity growth is less than 1% annually, so one has to essentially “push out” coal and eventually natural gas to make room for renewables. A technology to watch is utility scale electric storage which increased 40% in 2014 with 61.9 MW according to GTM Research and the Energy Storage Association. They estimate that 220 MW of electric storage will be installed in 2015. If utility scale electric storage takes off like renewable energy has, then renewables will take center stage and we will have less diversity in the electricity sector, although a much greener power sector. The larger question is whether we will have a more reliable electricity sector or one that is more susceptible to risks.
Future Cyber and Physical Security Risks in Reduced Carbon World
The energy sector will have to take a harder look at protecting the following resources in the next 10 years:
- Cybersecurity professionals will have to protect renewables and utility scale electric storage in the bulk power system as well as behind the meter. In places like California that has sizable distributed generation provided by residential solar panels, we will have to ensure that unsecured “behind the meter” assets don’t serve as a threat vector to utility scale power generation and storage resources.
- Security issues associated with utility scale and distributed electric storage devices will also have to be addressed. For example, Tesla Motors Powerwall will allow homeowners who generate electricity via solar panels or wind to store that electrical energy for latter use. As utility scale and behind the meter electric storage accelerates and becomes more important, cybersecurity professionals will have to pay greater attention to securing these assets.
- Cybersecurity professionals protecting coal fired generating plants will face increasing challenges from corporate management who don’t want to spend money to protect a generating asset scheduled for retirement.
- Some gas-fired combined cycle, combustion turbines and larger steam electric generating plants will face fuel security issues. Since these plants depend on pipelines to deliver just in time fuel, the risks associated with natural gas pipeline and compressor station outages will affect the reliability and risks of these power plants. These risks can be especially high during severe winters in regions where pipeline capacity can’t keep pace with natural gas demand for heating and power.
While the natural gas pipeline system is extensive and highly integrated with gas-fired power generation, many pipelines and associated compressor stations have been in the ground for decades. They are increasingly subject to leaks, explosions and fires which will affect the reliability of electric power and electricity prices if there are pipeline outages. Lets not forget damage to environmental resources either.
- Oil fired generating units are not ordinarily base load resources. So in most regions, these generating assets would be retired over time. However, operators will have to continue to maintain and protect these units in areas where they are used for winter electric reliability such as ISO New England and to mitigate natural gas price spikes. In some cases new power plants like Calpine's York 2 Energy Center power plant in the Pennsylvania are using oil fired generation for exactly the above reason.
If Only It Was Just a Cybersecurity Problem
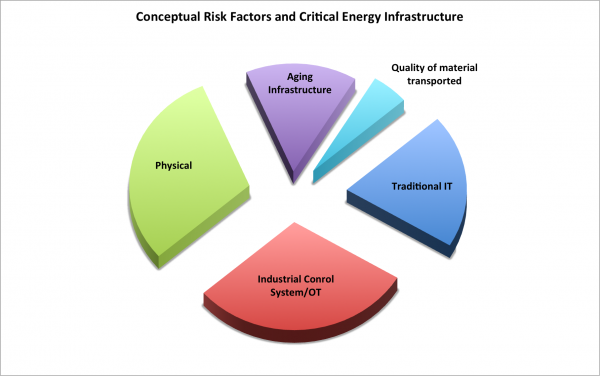
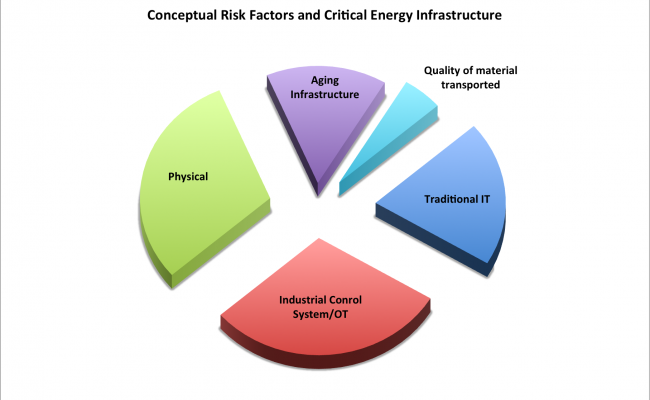
Perceived risks to an energy project are in the eyes of the beholder. To visualize risks to energy infrastructure, a conceptual model like the one below is helpful along with some examples.
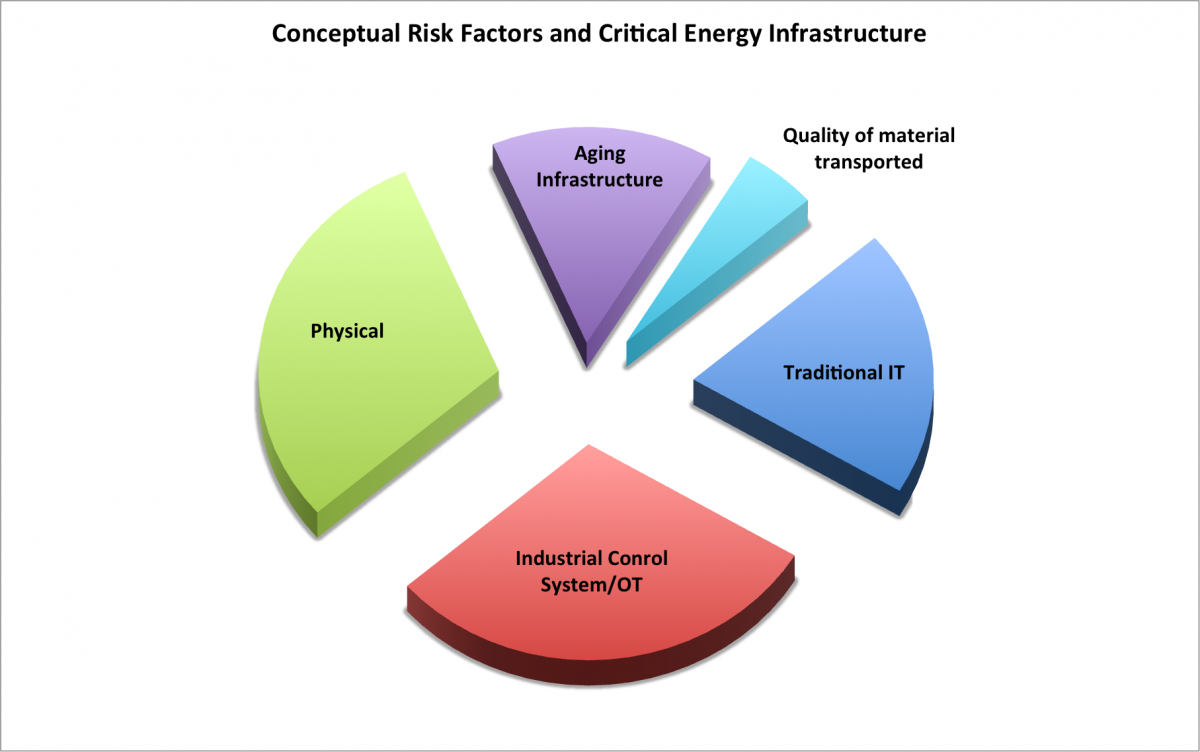
Source: Russo on Energy LLC
You'll notice that the above pie is exploded. While this improves readability, it also illustrates how stove piped energy companies are when it comes to protecting their infrastructure. A few examples follow.
To an engineer at an energy facility, risks may manifest themselves as vandalism, and overt attacks that result in a disruption of services and safety issues. Think kinetic attacks on power transformers, pipelines and compressors/pumps that result in explosions, fire, leaks and possible damage to the public and natural resources.
Industrial control systems staff that govern the operation of power plants, transmission lines, and pipelines are concerned with the availability of these systems and their reliability. They may perceive threats as someone from IT trying to patch their systems which could shut down the plant or an outsider/insider trying to exfiltrate information for later use. Corporate staff may consider the disruptions to energy operations with declining revenues and profits and increased liabilities.
While all of the groups perceive threats and risks differently, all should have a desire to promote the resiliency of the company’s assets. That means a focus on recovering quickly from a disruptive event. If energy infrastructure resiliency is high than disruptions to energy infrastructure will not result in higher physical natural gas and electricity prices or energy derivatives used to hedge risks.
What Energy Companies Should Do
Energy company CEOs, Boards, CIOs, Chief Information Security Officers and other involved in protecting energy infrastructure should focus more on the megatrends rather than just the Clean Power Plan. A key part is monitoring new energy technology and energy markets that improve reliability and green. Specifically, natural gas production and regional price trends as well as renewables growth and electric storage growth will dictate the pace of changes in the power sector and energy infrastructure investments. Besides, the Clean Power Plan will be systematically challenged in the courts and may take years to resolve.
Given the risks to energy infrastructure, companies can ill afford to continue to protect their energy assets in separate silos. Just like U.S. and international intelligence agencies, energy company staff responsible for protecting assets will have to share more information and collaborate with each other. Closing the information sharing and collaboration gap at an energy company is one of the most cost effective ways of strengthening a companies security program.
This is harder than it sounds since many companies have separate groups (Traditional IT, ICS/OT, Physical, Safety), cultures, vocabularies and perceptions of risk. Nevertheless, someone (CIO or the Chief Risk Officer) will have to unite and bring together these separate groups and make resiliency of critical energy infrastructure a common performance goal. Weekly meetings where all these groups share information and perceptions of threats to critical energy infrastructure are needed. Also automated systems that companies used to monitor and maintain energy assets are critical to facilitate the sharing of that information as well.